A survey on security in JXTA applications
Texto completo
Figure
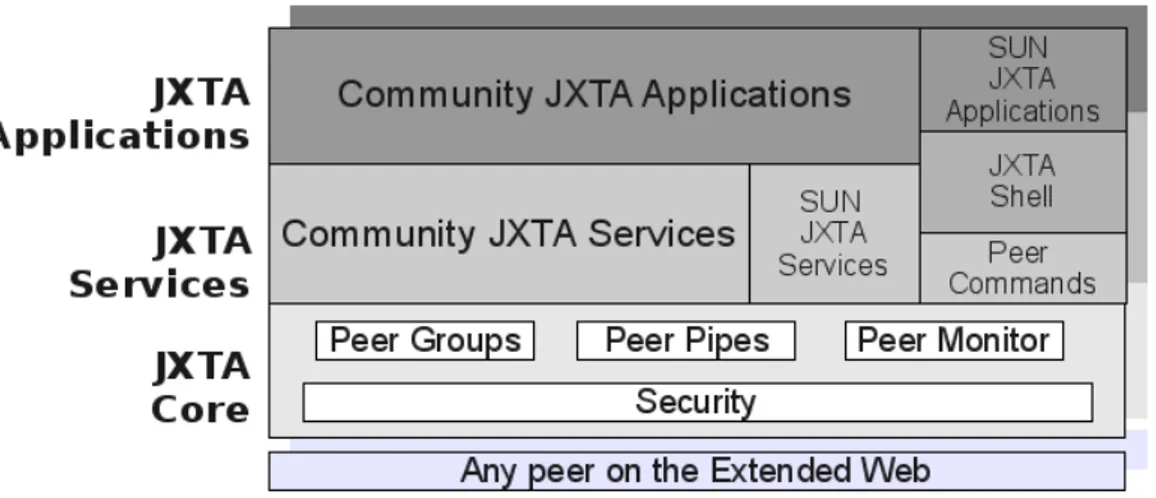


Documento similar
This better credit performance of companies run by women, coincident with their lower probability of obtaining a credit (10% in the first year, 8% one year later, and no difference
In working on a group, the problem of first and second canonical quantization on a (symmetric) curved space (which, relies heavily on both the structure of space-time itself and
(4) The fourth group includes the survey sites of Romance languages spoken in Friuli (both Italian and Friulian) and of the languages spoken in Sardinia (Sardinian, Catalan and
For instance, in a fully distributed model and using PMIPv6 terminology, each access router implements both LMA and MAG functions and for each user the access router could behave as
The expansionary monetary policy measures have had a negative impact on net interest margins both via the reduction in interest rates and –less powerfully- the flattening of the
Jointly estimate this entry game with several outcome equations (fees/rates, credit limits) for bank accounts, credit cards and lines of credit. Use simulation methods to
In our sample, 2890 deals were issued by less reputable underwriters (i.e. a weighted syndication underwriting reputation share below the share of the 7 th largest underwriter
In this paper, we seek energy saving opportunities in broadband access networks including: (i) on the user side, modem, wireless Access Point (AP), and router (hereafter