Defining security requirements through misuse actions
Texto completo
Figure
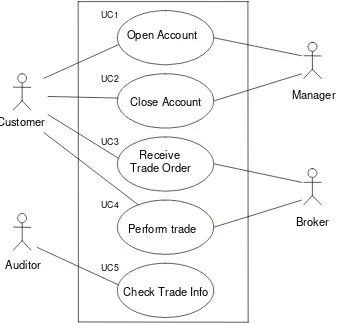



Documento similar
We are going to use Pasr Simple Tense for actions that start and finish in the past. Keywords: past actions,
No obstante, como esta enfermedad afecta a cada persona de manera diferente, no todas las opciones de cuidado y tratamiento pueden ser apropiadas para cada individuo.. La forma
The expansionary monetary policy measures have had a negative impact on net interest margins both via the reduction in interest rates and –less powerfully- the flattening of the
Jointly estimate this entry game with several outcome equations (fees/rates, credit limits) for bank accounts, credit cards and lines of credit. Use simulation methods to
In our sample, 2890 deals were issued by less reputable underwriters (i.e. a weighted syndication underwriting reputation share below the share of the 7 th largest underwriter
For this reason (and as we will show through- out this paper), we believe that if these security rules are specified on top of the underlying multidimensional model of the
The methodology developed for security management and its maturity in SMEs will allow any organization to manage, evaluate and measure the security of it information systems, but
The Dwellers in the Garden of Allah 109... The Dwellers in the Garden of Allah

