A Fair and Secure Cluster Formation Process for Ad Hoc Networks
Texto completo
Figure

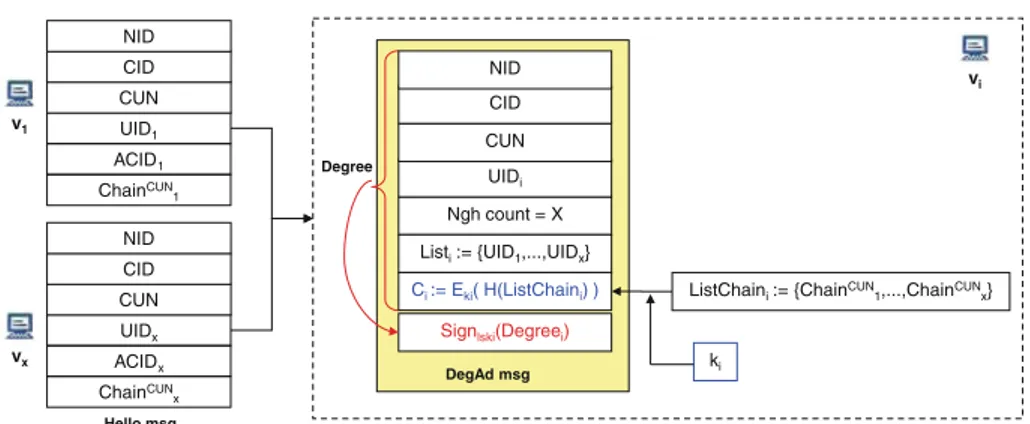
Documento similar
However, Zurieles, included in the late date of ripeness cluster in Madrid, seemed to be closer to the intermediate ripening date cluster when studied in Extremadura and compared to
In order to select the best cell line to be used in our neutralizing antibodies assay, the expression levels of the ACE2 receptor and the susceptibility of different cell lines to
Hence, with the initial configuration and the given budget, the number of security hosts needs to be increased by five units and the number of DB application hosts by two units in
These characteristics should be supported by the future network which should be able to handle higher bandwidth needs and to provide content adaptation in the network and
No obstante, como esta enfermedad afecta a cada persona de manera diferente, no todas las opciones de cuidado y tratamiento pueden ser apropiadas para cada individuo.. La forma
The expansionary monetary policy measures have had a negative impact on net interest margins both via the reduction in interest rates and –less powerfully- the flattening of the
Jointly estimate this entry game with several outcome equations (fees/rates, credit limits) for bank accounts, credit cards and lines of credit. Use simulation methods to
In our sample, 2890 deals were issued by less reputable underwriters (i.e. a weighted syndication underwriting reputation share below the share of the 7 th largest underwriter