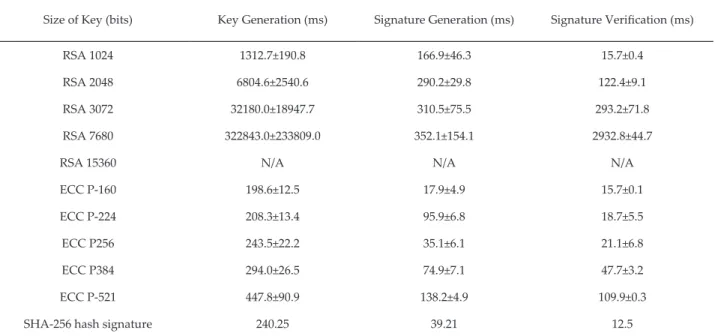
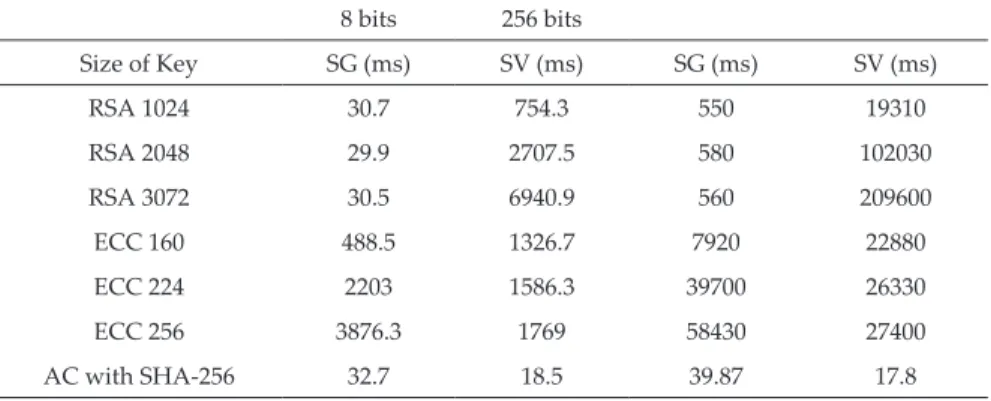
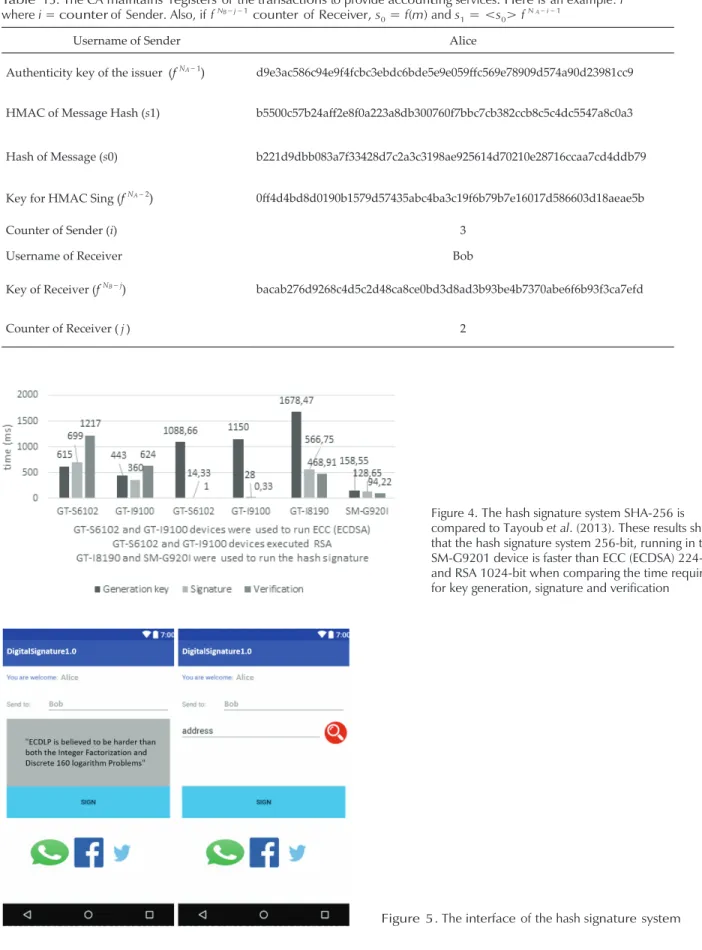
Revista Ingeniería Investigación y Tecnología | Facultad de Ingeniería UNAM
Texto completo
Figure

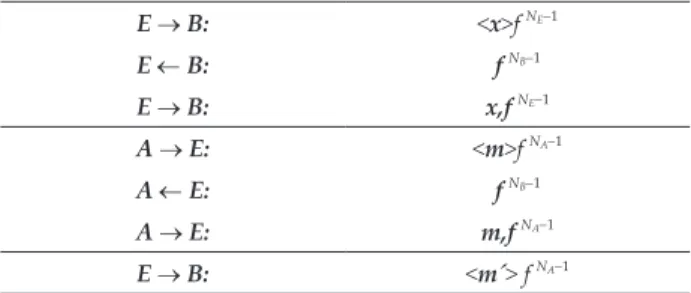

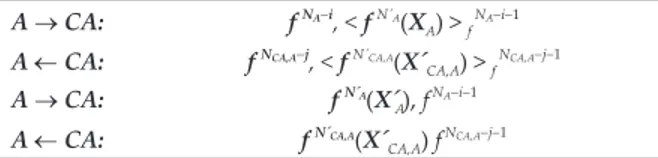
Documento similar
Regarding the two facial region extractors, it is inter- esting to see that some regions achieve a better perfor- mance for the extractor based on the proportions (both eyes,
To achieve it, firstly, a scale to measure the construct of the "organisational learning context" is supplied, and, secondly, it is explored if certain characteristics of
The s-CTMC is based on the CTMC 39 method, where the electron motion is described by a classical distribution, and it has been successfully applied to calculate ionization and
It will be explained the band-pass model based on impedance inverters [12] and it will be shown the structure of the filter using waveguide technology, since it is the technology
The design method is proposed for the nonlinear feedback cascade system, so it can be used for all the underactuated mechanical system that can be transformed to the cascade
The hash algorithm can, as shown in this section, be used for canonicalizing graphs, by using the partial hashes it computes for each statement and variable in the graph:.. • If
The result is indeed stated there only for L 1 (R N ) functions, but it is well known that the Calder´ on-Zygmund decomposition and weak type estimates for singular integrals work
Government policy varies between nations and this guidance sets out the need for balanced decision-making about ways of working, and the ongoing safety considerations