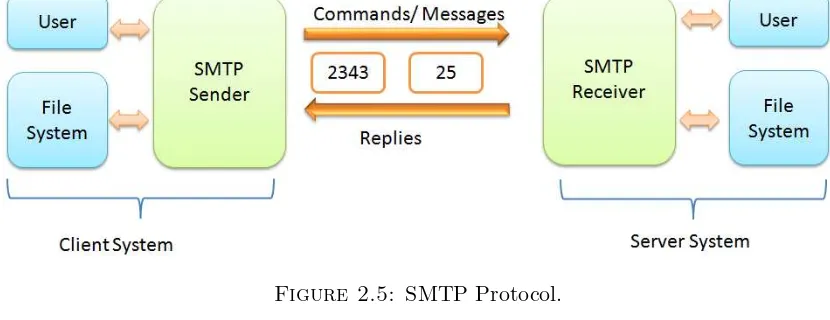
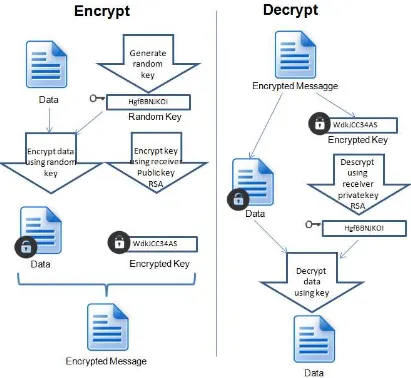
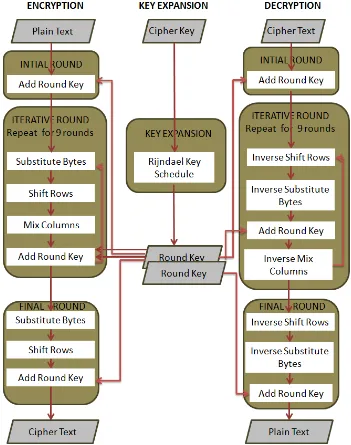
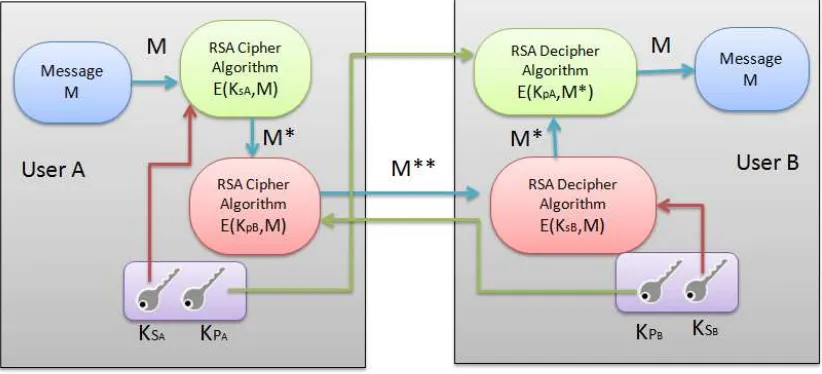
Implementación de una solución para evitar la pérdida de información en el uso de correos electrónicos corporativos
Texto completo
Figure


Documento similar
For this project, two different programs (MATLAB and DART) have worked together for recreating the radiance exchange of information between the Earth’s surface and the
• Exploration and implementation of new hardware architectures to improve some complex algorithms in the HiperLAN/2 chain, obtaining synthesizable models for the
• For those nodes and (mobile) routers with standard MIPv6 support, an address delegation mechanism, based on protocol for carrying authentication for network access (PANA) [15]
The expansionary monetary policy measures have had a negative impact on net interest margins both via the reduction in interest rates and –less powerfully- the flattening of the
Jointly estimate this entry game with several outcome equations (fees/rates, credit limits) for bank accounts, credit cards and lines of credit. Use simulation methods to
In our sample, 2890 deals were issued by less reputable underwriters (i.e. a weighted syndication underwriting reputation share below the share of the 7 th largest underwriter
(n = 147) of the students were studying either for the official degree in physical activity and sports sciences or for the official degree in primary education with a mention
In this paper, we present LOCUS, an H2020 project (https://www.locus-project.eu/) funded by the European Commission, aiming at the design and implementation of an innovative