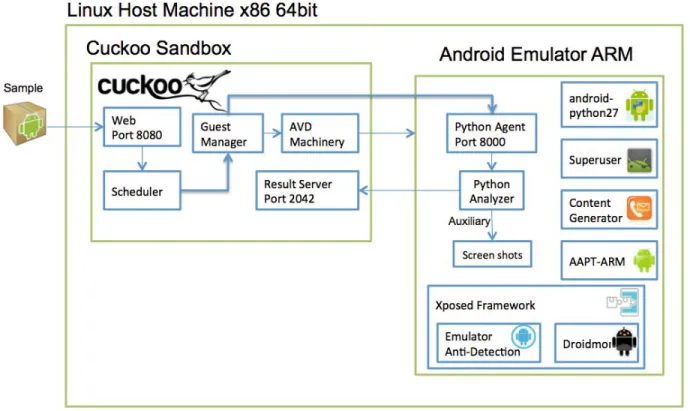
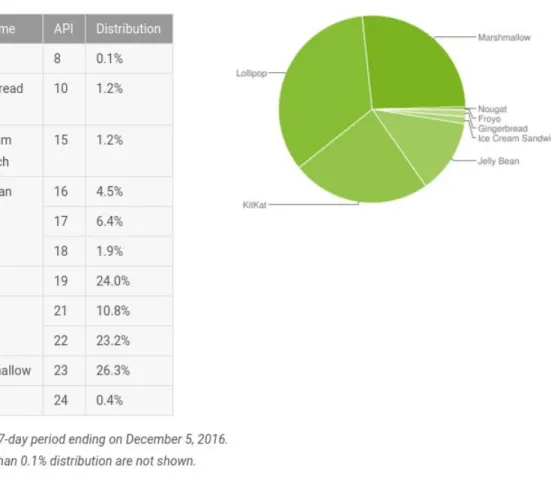
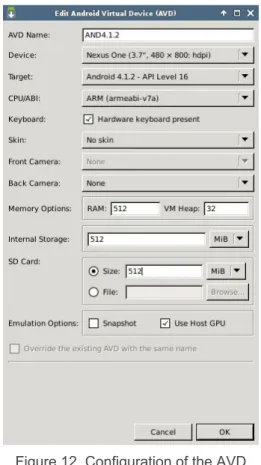
ANDRIK: Automated Android malware analysis
Texto completo
Figure
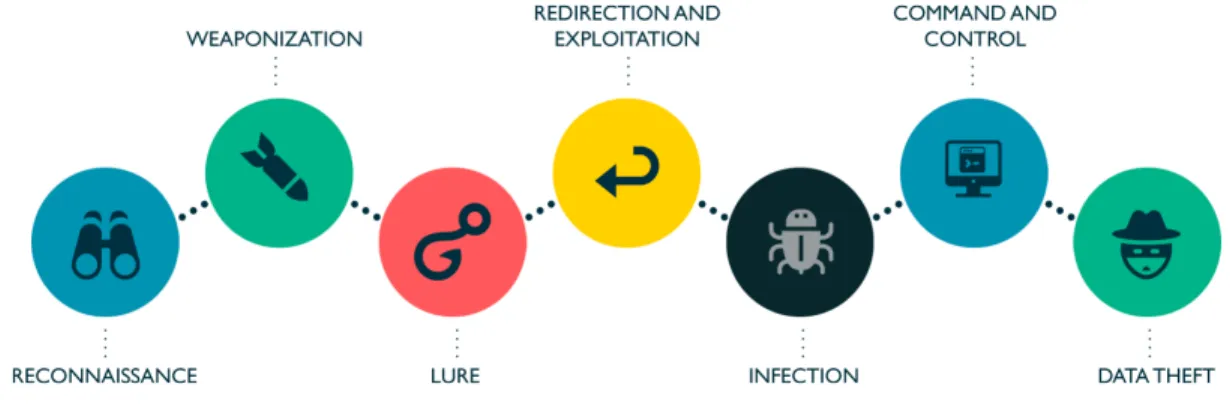
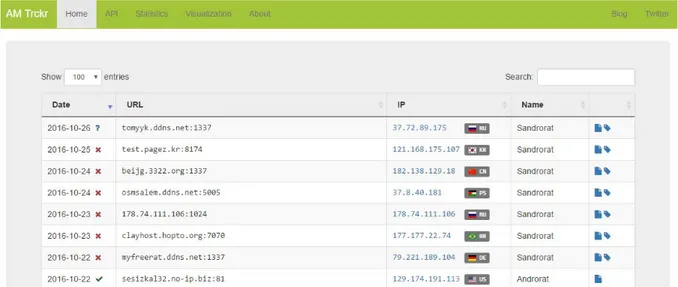
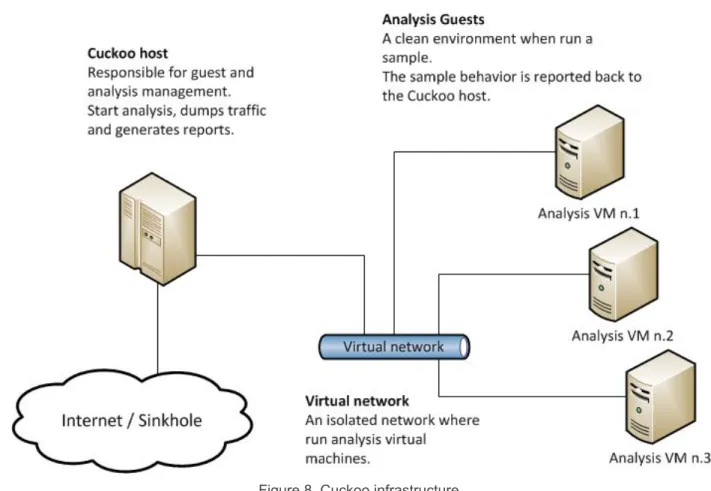
Documento similar
This paper aims to present Airbnb as an example of the sharing economy and analyze how its growth has been affecting the hotel industry and the rental housing market.. In order
(1) specification of the econometric model of the stochastic frontier, (2) selection of the inputs and outputs to use in the analysis, and (3) a determination about how
Government policy varies between nations and this guidance sets out the need for balanced decision-making about ways of working, and the ongoing safety considerations
This can make the experience of video calls even more tiring and difficult.. As a result of the factors mentioned above, people are at risk of what is now called “video
• Inadvertently, virtual water will play a greater role in food trade – simply as a function of increasing water scarcity and the disparity of water availability between countries
In this paper we describe how the knowledge related to a specific domain and the available visual analysis tools can be used to create dynamic visual analysis systems for video
This work shows, first, how the Labovian approach to personal oral narratives of “vivid” events is applied to emotionally charged texts and, second, how the theoretical concepts
The wound care doctors will instruct the patients about preventive measures to avoid infection or any complications from surgery as well as taking care of surgical wounds at home..
![Figure 14. Results of Virustotal for pizzachip[dot]com](https://thumb-us.123doks.com/thumbv2/123dok_es/7329448.357885/35.918.172.756.276.776/figure-results-of-virustotal-for-pizzachip-dot-com.webp)
![Figure 15. Results of Virustotal for a sample related to pizzachip[dot]com](https://thumb-us.123doks.com/thumbv2/123dok_es/7329448.357885/36.918.108.817.115.554/figure-results-virustotal-sample-related-pizzachip-dot-com.webp)