Privacy protecting systems for electronic commerce on mobile devices
Texto completo
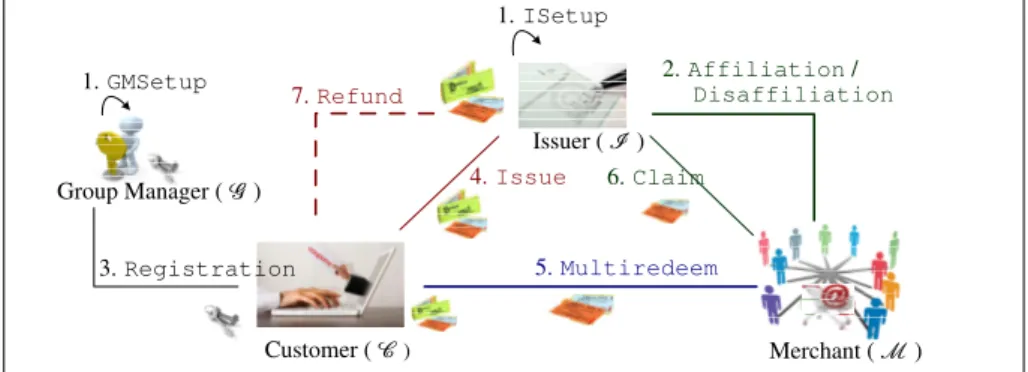
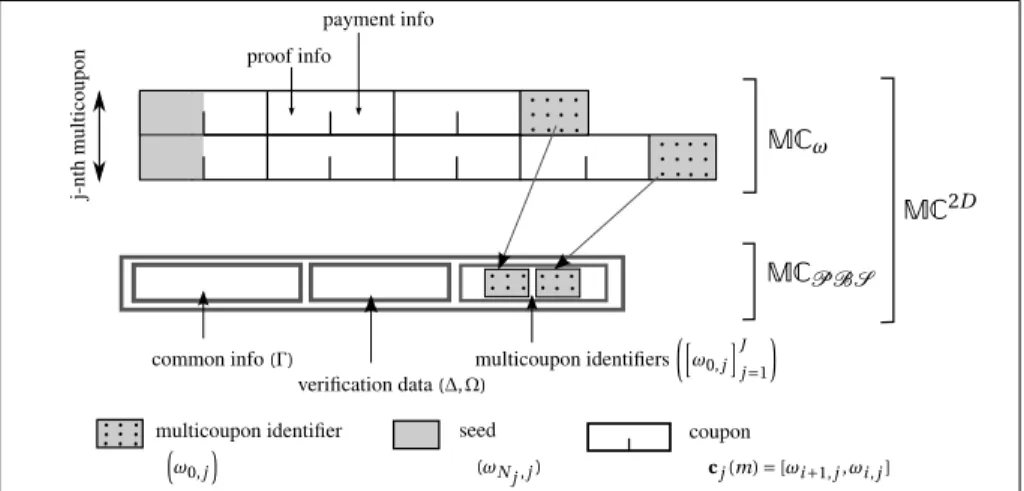
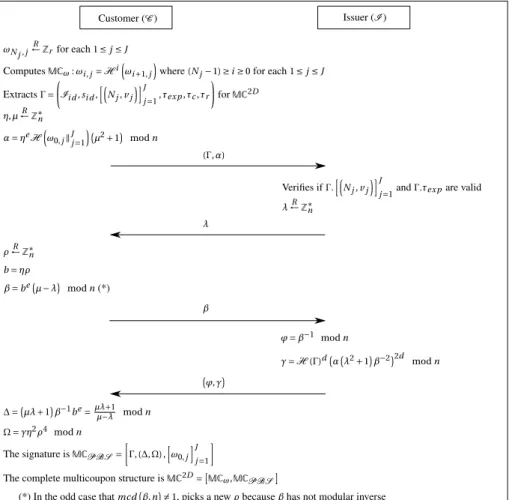
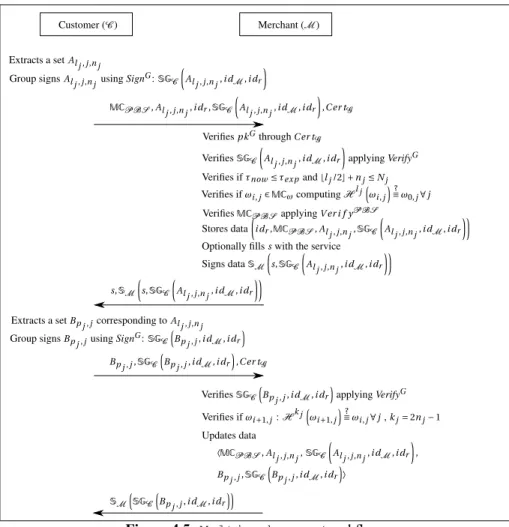
Figure

Documento similar
In order to enable flow mobility in a client-based mobile IP context, the IETF has standardized the basic components that are required. These components are: i) multiple care-of
In Chapter 7 we present two methodologies to derive three-outcome few-body symmetric Bell inequalities valid for many-body systems: (i) one based on projecting the set of
The paper is organized as follows: in section 1 we state and prove the extrap- olation results, in section 2 we state the commutator theorems, these theorems are proved in section 4,
We have proposed a method to detect outliers in multivariate continuous data based on projection into relevant subspaces by means of AA, applying a k-NN algorithm to these subspaces
It is interesting to highlight in both systems (global features-based and time functions-based systems) the case when the systems are trained and tested with DS3 and DS2 devices (DS3
In chapter 3, the overview and challenges of integrative –omics analysis and the main statistical methods that have been used for data integration is described and in chapter
As a first step to reach our objectives, in Chapter §3 we have performed a detailed analysis of all data taken by the XMM-Newton satellite of UGC 11763 to characterize the
In this chapter we have studied how the current identification procedures in active devices have a low performance due to the use of anti-collision techniques from passive RFID