TítuloReverse Engineering and Security Evaluation of Commercial Tags for RFID Based IoT Applications
Texto completo
Figure



Documento similar
Concerning related work, we are unable to compare our tool due to the fact that, as far as we know, there exist four SPE tools [3, 2, 10, 15] based on UML and none of them
The latter is a modeling language intended for model-driven development of component- based software systems and for the early evaluation of non-functional properties such as
Finally we observe that several types of analysis can be con- ducted on the models built with this approach: (i) a performance model with a set of security requirements can be
We propose a handover detection scheme based on the analysis of the GN header of data packets instead of Neighbor Discovery messages. Since RSU/MAGs are the gateways of vehicles
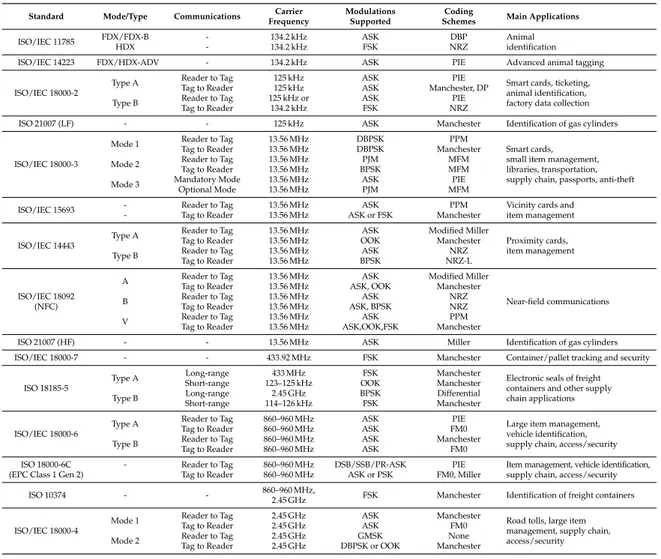
This thesis is framed within the RFID technology and has been focused on the design of tags and near field communication devices to operate within the UHF-RFID frequency band,
Seabirds (Laridae) as a source of Campylobacter spp., Salmonella spp. and antimicrobial resistance in South Africa. An evaluation of three commercial fecal transport systems for
Centre de Recerca en Sanitat Animal (CReSA). However, mark loss or mark-induced mortality can introduce biases and decrease precision in parameter estimates, leading to
We analyze the problem when a change is caused by an existing node in the network that announces a new route as an alternative to a one already trustable route. Once the